Classification of files and documents - Kunnskapsbasen
Classification of files and documents
This page contains information on how to classify files and information according to confidentiality requirements, using sensitivity labels in Word, Excel, PowerPoint and Outlook.
Norsk versjon - Klassifisering av filer og informasjon
Topic page about Information security | Pages labeled with classification
Innholdsfortegnelse [-]
Information classification
All information processed at NTNU must be classified according to confidentiality requirements, so that you know where and how the information can be processed. You can find more information about information classification in the Policy for Classification of Information Assets
The following classes are defined:
Sensitivity labels in Word, PowerPoint, Excel and Outlook
In Microsoft 365, it is possible to determine the classification of files and documents, through the use of "sensitivity labels" that mark the documents and which can trigger technical measures such as encryption. We use Azure Information Protection (AIP) to enable this feature. Once AIP is installed, you will find the classes as Sensetivity in the desktop version of Microsoft 365.
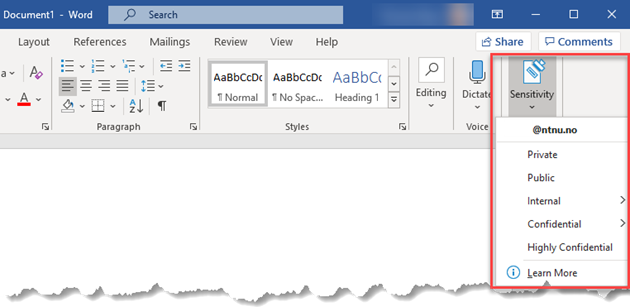
Public
This label applies to information that may be accessible to anyone, without special access rights.
Examples of such information may be web pages, course listings or printed material that is freely distributed.
Internal
Information which requires some protection and where accessibility should be restricted to selected internal and / or external users, with controlled access rights, can be classified as Internal. Can be used if it could cause some damage to the institution, or partners if the information becomes known to unauthorized persons.
Examples of such information are some working documents, information that is kept from public access, personal information, grades, large student papers, exam answers, research data and research work.
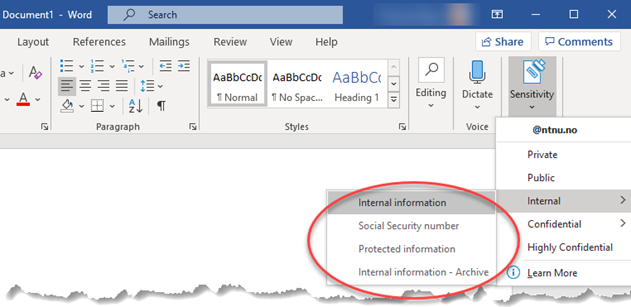
- Internal information must be categorized into one of three subcategories. When using the Internal information category, no technical restrictions are imposed on the document. This means that anyone who has access to where the file is stored will have access to the document.
- Using the Social Security number or Protected information categories, the document is encrypted and access control is logged. The category Social Security number should be used on documents that contain a social security number. The cateroty Protected information can be used on documents when you want encryption and access control, even if it does not contain a social security number or can be classified as confidential.
- The category Internal information - Archive is used exclusively to remove encryption before a document is archived in ePhorte.
Confidential
Documents containing confidential information should be classified using the label Confidential. This includes information that requires strict access control. Must be used if it may cause harm to public interests, the institution, individuals or partners if the information becomes known to unauthorized persons.
Examples of such information are some strategy documents, sensitive personal information, health information, exam papers before they are given, some types of research data and work.
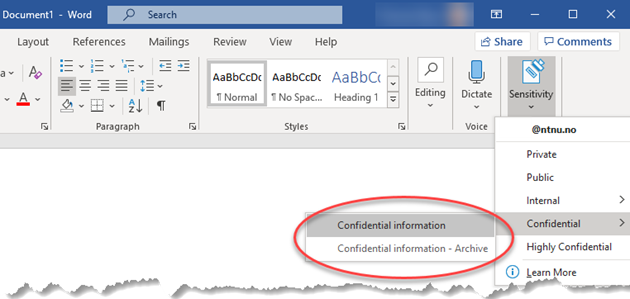
When the Confidential label is used, several technical restrictions are applied on the document:
- The document is encrypted and access control with log is activated.
- It will not be possible to print or take a screenshot of the document.
- The label Confidential - Archive is used exclusively to remove encryption before a document is archived in ePhorte.
Note that it is not yet possible to open documents with access control in Microsoft 365 Online (browser version).
Highly Confidential
The label Highly Confidential should not be used. Documents with information in this class must be processed in systems that are approved for this.
Private
Any private documents can be labeled Private.
Grant permissions
In Word, Excel and PowerPoint
When using the label Confidential and when using the categories Social Security number or Protected information under the label Internal, you must grant permissions on the document.
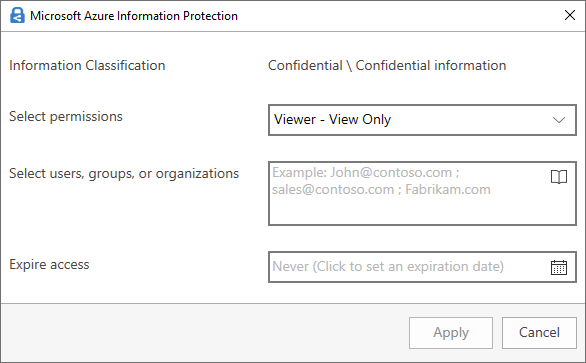
In the Select permissions field, specify the permission you want to grant:
- Viewer - View only
- Reviewer - View, Edit
- Co-Author - View, Edit, Copy, Print
- Co-Owner - All permissions
- Only for me
Then point out who gets the appropriate permit, by entering their email adress(es). Do not use groups when granting permissions. In the bottom field, you can specify an expiration date if desired.
In Outlook
When using the sensitivity label Confidential and when using the categories Social Security number or Protected information under the sensitivity label Internal, the email is encrypted. Permissions are granted to recipients of the email.
Note: Avoid using email lists and groups as recipients in email when encryption is used. The reason is that access is linked to individuals through the recipient's email address. Content is only decrypted when the recipient is authenticated with their personal user. The use of groups will therefore make the content unreadable to recipients.
Change or delete sensitivity label
If a sensitivity label is already used on a document and you want to change it, you can just select another label. To delete a sensitivity label from a document, click the already selected sensitivity label in the Sensitivity menu.
Installation and use on various devices
Windows
AIP has to be installed from Software Center on NTNU machines with Windows operating system. If you have a standalone Windows machine (unmanaged) you can install the AIP client yourself from Microsoft.
Mac
Classification by using sensitivity labels is also supported in Microsoft desktop applications on Mac. No installation is required. The sensitivity labels can be found under the menu option Home and the Sensitivity button.
Android and iOS
With the Word, Excel and PowerPoint apps, you can read and edit classified documents and protected documents, from mobile phones and tablets. However, you cannot classify documents with sensitivity labels that cause encryption in these apps.
Outlook on mobile allows you to read the contents of encrypted emails, but you can not send encrypted messages from your mobile.
If you use a program other than Outlook to read email, you can read the contents of encrypted email messages (.rpmsg files) by using the Azure Information Protection app. This app also allows you to open other file types with access control, such as PDFs or image files.
Software Farm
Users with machines that do not directly support classification can use the service from Software Farm.
Encryption and external users
AIP is initially intended as a service for classification of information internally at NTNU, but it is possible to encrypt e-mails and documents to external recipients as well. However, this requires that the recipient's email address can be authenticated to Microsoft (Azure AD or MS account). The reason is that the sender's and recipient's email address is their key to decrypt documents and emails that are encrypted using NTNU's certificate.
Can data be decrypted?
The solution is configured with an encryption key issued by Microsoft. This means that there is a theoretical possibility that Microsoft can decrypt content. A limited group of our own administrators can also temporarily allow themselves to decrypt content. This can for example be required if a file is encrypted and archived in ePhorte by a former employee. Such activity is continuously logged. If you are interested in more technical information, you can read about her.
Concerning filing in ePhorte
Documents
- ePhorte has its own access control system and documents there should not be classified using sensitivity labels.
- Encrypted documents must be decrypted before filing in ePhorte. The person who encrypts the document (the document owner) must consider whether it should be archived in ePhorte.
- Use the label caterories Internal information - Archive or Confidential information - Archive to remove encryption before archiving. If you want to keep the original file after archiving, the correct label must be re-inserted. Alternatively, the file can be deleted.
- To import encrypted email into ePhorte, the EphorteOutlook program must be used. It is not possible to import encrypted email using "Importsentral" in ePhorte.
- Any attachments in encrypted email must be decrypted before filing in ePhorte.
More information
You can find more information about AIP on Microsoft's website.
Contact
Orakel Support Services can help if you have questions or if you encounter difficulties.
